Security & Compliance
Best-of-Breed Security features are leveraged within Dynamic DSM’s energy rebate solution. This includes system access, system controls, handling & avoidance of human error, handling solutions, data validation and verification, system audit trails, security roles and teams, conditional screen security and more.
Microsoft has designed security, data protection, reliability, and privacy of the Microsoft Dynamics CRM Online around high industry standards. Microsoft Dynamics CRM Online and the infrastructure on which it relies (Microsoft Global Foundation Services) employ security frameworks that are based on the International Standards Organization (ISO/IEC 27001:2005) family of standards and are ISO 27001 certified by independent auditors. Microsoft’s ISO 27001 certifications enable customers to evaluate how Microsoft meets or exceeds the standards and implementation guidance against which Microsoft is certified.
While Microsoft is responsible for provisioning instances of Microsoft Dynamics CRM Online, customers take on responsibility for controlling and maintaining their business environments (i.e. user access management and applying appropriate policies and procedures in accordance with their regulatory requirements) after provisioning is complete. To accomplish this, customers can leverage features and capabilities built in to Microsoft Dynamics CRM to accommodate compliance with a wide range of regulations and privacy mandates.
Auditing and System Tracking
Auditing in Microsoft Dynamics CRM can be configured at three levels: organization, entity, and attribute (listed here in hierarchical order). Auditing and reporting are the keys to understanding what happens to data that is not under the organization’s direct control. Without them, it is difficult to roll back unwanted or fraudulent transactions. Auditing also forms the basis for compliance regimes. Here are the main concerns in this area:
- Audit scope. What is audited in the service? How comprehensive are the audits, and how long does audit information persist? Is user information persisted for forensic analysis? Can audit information be used to roll back improper transactions? Do audits conform to relevant laws, regulations, standards, and industry best practices?
- Audit integrity. How is audit information protected? Who has administrative access to it? Is the audit information stored in a protected and reliable manner?
- Reporting. Is the audit information easily accessible? Does it have sufficient scope for compliance and governance controls? Is the information usable as a forensic artifact for legal purposes?
Field-Level Audting. Dynamic DSM provides auditing for every record and even down to each field in the system. Field-level auditing provides the following information:
- Field Name
- Previous Value
- New Value
- User who performed the updates
- Date and Time of the update
Viewing the Audit Summary The history of audited data changes to a record or attribute is stored in the records associated with the audit entity. For each entity that has been enabled for auditing, the audit summary shows the change details of all audited records, which are listed in a chronological order, starting with the most recent ones. The ability to retrieve and display the audit history is restricted to users with specific security privileges: View Audit History and View Audit Summary. There are also privileges specific to partitions: View Audit Partitions, and Delete Audit Partitions.
Identity & Access Control
Identity and access control is one of the most overlooked and difficult IT tasks, but it also can have the most direct impact on information protection. Dynamic DSM allows our customers to establish effective identity and access control. This typically involves consideration of the following components:
- Identity provisioning. An organization’s IT practices should integrate with those of the CSP so that no security gaps exist around provisioning new users, creating trust relationships for access control, and de-provisioning users whose status has changed. Authentication. The CSP should support different levels of authentication depending on the customer perception of the nature of the service and the sensitivity of the data entrusted to the service.
- Single sign-on. Single sign-on, also known as identity federation, allows an organization to enhance privacy and while at the same time providing the greatest flexibility. Using single sign-on, the customer organization maintains complete ownership and control of business critical portions of the access control stack.
- Standards. To achieve the requisite level of federation and application portability, organizations should evaluate the CSP’s adherence to industry standards governing identity, authentication, authorization, and access.
- Auditability. All access-control decision points should be auditable to easily identify unauthorized access, and hold unauthorized users accountable. This would include unauthorized access by means of administrative credentials maintained by the CSP.
- Information Protection & Data confidentiality. Whenever possible, encrypt (and decrypt) confidential data during on premises or end-point processing before it is transferred to the cloud. The key goal is to protect data confidentiality in an end-to-end manner.
- Basic data integrity. Key concerns include infrastructure reliability, access controls, and commingling of data.
- Data availability. Service availability requirements should be defined. In addition, should data becomes corrupted, alternative storage, backup, or other mechanisms should be available to protect the information.
- Data persistence. Issues of data persistence include making backups, maintaining multiple copies, and using virtual machine images, all of which may contain sensitive data.
Security Teams and Roles
Role-based security relates to establishing security roles, each of which groups together a set of privileges that represent the responsibilities of (or tasks that can be performed by) a user. For example, a user that has been assigned the System Administrator role can perform a wider set of tasks (and has a greater number of privileges) associated with viewing and modifying data and resources than can a user who has been assigned to the Salesperson role. A user assigned the System Administrator role can, for instance, assign an account to anyone in the system, while a user assigned the Salesperson role cannot. Teams can also be assigned a security role and can own Microsoft Dynamics CRM records. Microsoft Dynamics CRM does not require a specific user to be the record owner. This reduces the amount of record ownership housekeeping required from administrators when users change business units, teams or leave the company. Microsoft Dynamics CRM includes a set of predefined security roles, and when users are created in the system, each user must be assigned one or more security roles. Dynamic DSM provides endless flexibility for configuring security access:
- Security Roles

- By Field
- By Module
- Security Teams
- Territories
- Teams
- Business Units
- Data segregation
- Record-Based Security
- Field-Level Security
Risk & Compliance
With on-premises deployments of Microsoft Dynamics CRM, customers have control of and responsibility for their environment from end-to-end. However, customers contemplating a move to the cloud with Microsoft Dynamics CRM Online often raise questions about security, data protection, privacy, and data ownership. Microsoft takes these concerns seriously and has applied its years of cloud and on-premises experience with security and privacy to development of its online services offerings, including Microsoft Dynamics CRM Online.
The Microsoft Dynamics CRM Online service provides secure access across platforms and
devices, with anti-spam and antivirus technologies that are automatically updated to protect against the latest threats. The security features and services associated with Microsoft Dynamics
CRM Online are built in, which can help to reduce the time and cost associated with securing
customer IT systems. At the same time, Microsoft Dynamics CRM Online enables administrators.
- Data Confidentiality
- Data Integrity
- Data Availability
- Data Persistence
Flexible Security Features
Dynamic DSM contains multiple layers of Security:
- Configurable strong password rules
- Role-Based access controls
- Granular permission assignment
- User-based field-level security (system-wide)
- Data-based field-level security (conditional based on specific record criteria)
- Milestone user security
- Approval level security
- Field Auditing – tracking which user made what changes at what time (configurable for each Entity and each individual field)
Advanced Solution Management
Microsoft Dynamics CRM allows users to create and test features thoroughly in a Development environment and then move a “Solution Package” into the Production environment after it has passed all tests, helping to minimize risk.
Securing the Business Environment
Microsoft Dynamics CRM Online includes several features that provide administrators with the ability to implement a variety of IT controls, which some IT controls can be implemented by using the platform on which Microsoft Dynamics CRM Online is installed. As a result, it is important that the compliance team within an organization clearly define the IT controls that need to be implemented to ensure compliance. The following sections review key areas of a business solution for which the features provided in Microsoft Dynamics CRM Online can be used to implement IT controls.
Securing the On-Premise Server Infrastructure
One of the most critical steps in establishing a secure business environment is to ensure that the software platform on which the solution will rely is secure and up-to-date. When evaluating platform security, consider the following best practices:
- Use the latest operating system with current service packs.
- Install the most current security patches.
- Install antimalware software.
- Minimize the operating system surface area for attack:
- Limit running services.
- Install only software needed to support server role.
- Disable unnecessary ports.
- Configure the firewall.
- Limit number of users with access to the server and the number of roles per user
Physical safeguards for on-premises components
Implementing physical safeguards goes hand-in-hand with virtual or software-based security measures, and similar risk assessment and mitigation procedures apply to each. Organizations should use various measures to help protect their operations from power failure, physical intrusion, and network outages. These measures should comply with industry standards for physical security and reliability and be regularly managed, monitored, and administered by operations staff.
Integration with line-of-business applications
An important part of designing a compliant business solution is to ensure the secure operations of any on-premises line-of-business applications that will be integrated into the Microsoft Dynamics CRM Online solution. In some cases, an organization may need to make changes to the applications or custom code to ensure that it functions properly with Microsoft Dynamics CRM Online.
Protecting user credentials stored on the CRM Email Router
Microsoft Dynamics CRM Online business solutions, while cloud based, still require that an organization maintain select components in their on-premises environments. One such component is the Microsoft Dynamics CRM Email Router, which serves as an interface between Microsoft Dynamics CRM Online and one or more Microsoft Exchange servers, or POP3 servers, for incoming e-mail, and one or more SMTP servers for outgoing e-mail.
Single sign-on in Microsoft Dynamics CRM Online
Single sign-on, also called identity federation, allows customers to use credentials associated with their AD based domain user accounts to access Microsoft Dynamics CRM Online and other Microsoft online services. This type of identity management is useful for large organizations with hundreds of thousands of established users, as it avoids the need for administrators top re-create user identities in the cloud.
Data accessibility for Microsoft Dynamics CRM users
The Microsoft Dynamics CRM security model protects data integrity and privacy as well as supporting efficient data access and collaboration. The goals of the security model in Microsoft Dynamics CRM Online are to:
- Provide users with the access only to the appropriate levels of information that is required todo their jobs.
- Categorize users by role and restrict access based on those roles.
- Support data sharing so that users and teams can be granted access to records that they do not own for a specified collaborative effort.
- Prevent a user’s access to records that the user does not own or share
Additional Security Options
- Ability to host on premise behind a Firewall
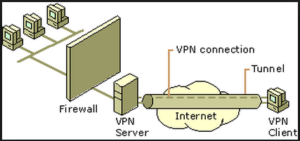
- Option to limit access to VPN
- Option to limit logins to Remote Desktop (RDP) or Terminal Service
- Option to limit the IP addresses allowed to access
- SFTP
